Print Fix Hub
Your go-to source for everything print-related, from troubleshooting to tips.
Whispers in the Blockchain: How to Keep Your Bitcoin Transactions Private
Unlock the secrets to private Bitcoin transactions! Discover how to safeguard your crypto with our expert tips on blockchain privacy.
Understanding Bitcoin Privacy: Tips for Securing Your Transactions
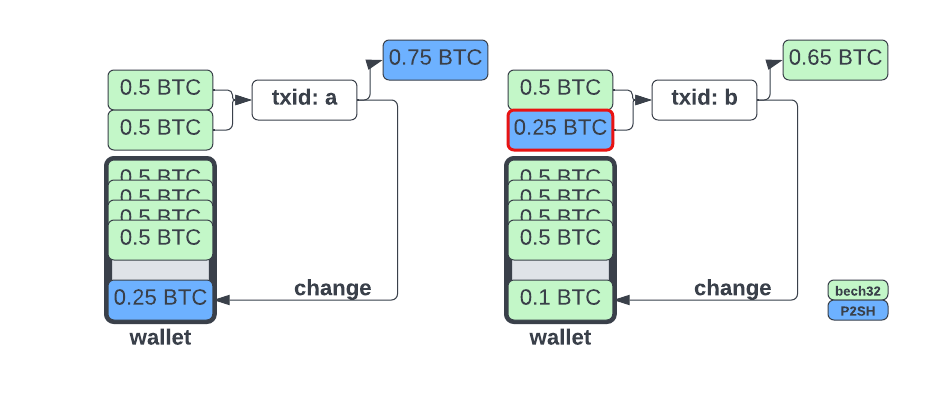
Understanding Bitcoin privacy is essential for anyone looking to secure their cryptocurrency transactions. While Bitcoin transactions are often viewed as anonymous, they are actually pseudonymous, meaning that transaction details are publicly available on the blockchain and can be linked back to user identities. To enhance your Bitcoin privacy, consider using privacy-focused wallets that support features like coin mixing and stealth addresses. These tools can help obscure your transaction history and protect your personal information from prying eyes.
In addition to using specialized wallets, you can also adopt practices that promote privacy in your Bitcoin transactions. For instance, avoid reusing addresses, as this can create a clear link between multiple transactions and your identity. Additionally, consider using a VPN or Tor to mask your IP address when making transactions. Regularly expanding your knowledge on Bitcoin privacy techniques and staying up-to-date on the latest developments can significantly bolster your security.
Counter-Strike is a popular first-person shooter game that has captivated millions of players worldwide. It features team-based gameplay, where players can choose to be part of either the Terrorists or the Counter-Terrorists. For those interested in enhancing their gaming experience, exploring options like cloudbet promo code can provide beneficial perks.
The Importance of Anonymity in Cryptocurrency: What You Need to Know
The rise of cryptocurrency has transformed the way we perceive and conduct financial transactions. One of the primary benefits driving this transformation is the anonymity that many cryptocurrencies provide. This anonymity ensures that users can engage in transactions without revealing their personal identities, which is essential for protecting privacy in an increasingly interconnected world. As concerns about data breaches and surveillance continue to grow, the demand for anonymity in cryptocurrency is becoming more pronounced, with users seeking refuge from intrusive tracking and potential misuse of their financial data.
However, the importance of anonymity in cryptocurrency extends beyond mere privacy. It also plays a pivotal role in promoting freedom and independence in financial transactions. By using cryptocurrencies that prioritize anonymity, individuals can partake in an uncensored economy, free from governmental control and intervention. This level of autonomy can empower users, particularly in regions where traditional banking systems are unreliable or where financial oppression exists. The balance between anonymity and regulatory frameworks is delicate; understanding this relationship is crucial for anyone looking to navigate the evolving landscape of digital finance safely and effectively.
Common Myths About Bitcoin Privacy: Debunking Misconceptions
Many people believe that Bitcoin transactions are completely anonymous, which is one of the most prevalent myths about Bitcoin privacy. In reality, while Bitcoin does not directly link transactions to personal identities, it operates on a public ledger known as the blockchain. This means that every transaction is recorded and can be traced through the network. If a user's wallet address is ever tied to their real identity, all associated transactions become transparent and can be followed. Thus, while it offers a degree of privacy, it is not as anonymous as some may think.
Another common misconception is that using a mix service or a privacy coin guarantees complete privacy. While these methods can enhance Bitcoin privacy, they are not foolproof. Mixing services, for example, can reduce the traceability of transactions but do not eliminate it entirely. Law enforcement agencies are also becoming more adept at tracking such transactions. Privacy coins might obscure transaction details better than Bitcoin, but they can still attract attention due to their alternative nature. Therefore, it's crucial for users seeking true privacy to understand that no method is entirely secure.